Configuring Target Servers for
Deployment
See also: Deployment Overview, Designer Preferences
Deployment
Security Requirements
Target Servers for deployment can be configured using the Deployment Wizard during a deploy operation or using Designer Preferences Deployment tab.
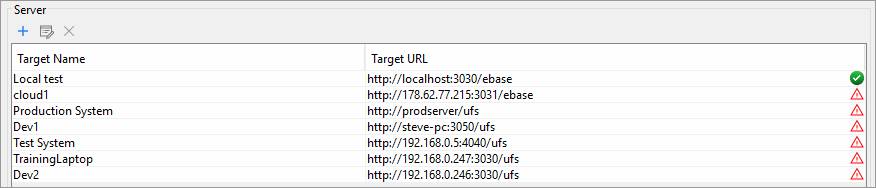
The icon in the right-hand column shows whether the target
server is currently available, and this is only shown during deploy operations.
Click the ![]() icon to create a new target server or
icon to create a new target server or ![]() to edit an existing target server. Both options
show the Configure target server
dialog:
to edit an existing target server. Both options
show the Configure target server
dialog:
|
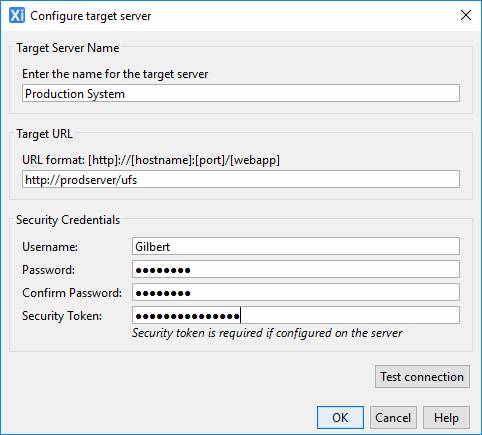
Target Server Name |
Enter any name of your choice; this name is shown each time you select a target server |
|
Target URL |
The URL of the target system up to and including the web application name e.g. http://testserver:3031/ebasetest |
|
Security
Credentials |
User name and password on the target server. See Deployment Security Requirements below. Security Token is required when server deployment property Deployment Security Token is specified, and must then match the server token value. |
Click the Test connection button to test that the configuration is correct and a connection can be made to the target server.
Deployment Security Requirements
To deploy successfully to a target server, the following security requirements must be met:
1. The user is defined within the Ebase Security System on the target server with the correct password. Users can be added and maintained using the Server Administration Application – Ebase Security System. It is not currently possible to use users defined externally for deployment e.g. Windows domain users.
2. The user has the DEPLOY role. This role is included within the standard Ebase Xi distribution.
3. If a Deployment Security Token is specified on the server, the same token value must be specified here.
**Important Note: When a server is available on the public internet, care should be taken to ensure that user/password combinations cannot be guessed. In particular:
- Avoid the use of simple (guessable) user names and passwords
- Do not use the supplied ebaseuser user for deployment
Also specify a deployment security token as an additional security check.
If the possibility of rogue deployments is still a concern, then set the Hold deployments on server option using the Server Administration Application – Deployment Properties.